Splunk Forwarder The forwarder is an agent you deploy on IT systems, which collects logs and sends them to the indexer. Each type should get its own forwarder, its own prefix (directory) in the S3 bucket, its own SQS queue, its own Splunk input, and its own Splunk Source Type. In front of monitor specify remote log file location. 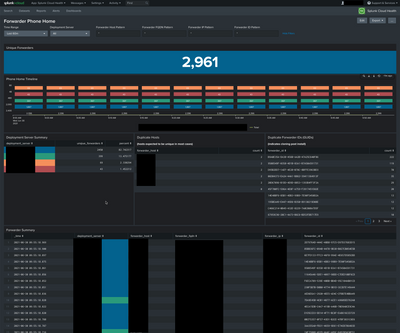
 Through various methods and mediums, be it digital webinars, local and regional user groups, or one-on-one private meetings, our Experts are prepared to tackle the unique challenges that plague specific industry verticals, and share intelligence on the latest security threats and threat actors. From the IAM Role tab, add the Role ARN provided by your AWS team. And outputs.conf is the configuration file that controls sending the dataout tothe indexing server or Splunk Receiver. Acts as intermediary in routing data, Does not parse data (except when the data is structured such as CSV), Parses data, which includes Line breaking, timestamp extraction and extracting index-time fields, Built-in license. In Unix servers, the Splunk Universal Forwarder runs as a process named splunkd. To confirm the configuration is working end-to-end, use the Health Check ->Health Overview dashboard in the Splunk Add-on for AWS. The Splunk Universal Forwarder binary is somewhat similar to that of Splunk Indexer or Search Head, but it is stripped down bare-bone version. Verify the index name is set as you expect: This likely means the Data Forwarder is writing to S3 and S3 is writing new object notifications to SQS. Splunk forwarderis one of the components of Splunk infrastructure.
Through various methods and mediums, be it digital webinars, local and regional user groups, or one-on-one private meetings, our Experts are prepared to tackle the unique challenges that plague specific industry verticals, and share intelligence on the latest security threats and threat actors. From the IAM Role tab, add the Role ARN provided by your AWS team. And outputs.conf is the configuration file that controls sending the dataout tothe indexing server or Splunk Receiver. Acts as intermediary in routing data, Does not parse data (except when the data is structured such as CSV), Parses data, which includes Line breaking, timestamp extraction and extracting index-time fields, Built-in license. In Unix servers, the Splunk Universal Forwarder runs as a process named splunkd. To confirm the configuration is working end-to-end, use the Health Check ->Health Overview dashboard in the Splunk Add-on for AWS. The Splunk Universal Forwarder binary is somewhat similar to that of Splunk Indexer or Search Head, but it is stripped down bare-bone version. Verify the index name is set as you expect: This likely means the Data Forwarder is writing to S3 and S3 is writing new object notifications to SQS. Splunk forwarderis one of the components of Splunk infrastructure.
Requires access to Enterprise license stack if indexing is required. Finally, if you need forward data to a third-party data store, use Heavy Fowarders. They can scale to tens of thousands of remote systems, collecting terabytes of data. While nothing is impossible in the complex world of IT, I can confidently say that Splunk Universal Forwarder is one of the most efficient software you will find out there. VMware Carbon Black Cloud Workload delivers advanced workload protection purpose-built for securing modern workloads to reduce the attack surface. At Tech Zone, we've made it our mission to provide you with the resources you need, wherever you are in your security journey. How to obtain heap dump and core dump in Jboss ? You can gain insight into and respond faster to attacks with Carbon Black Cloud Managed Detection and Response, which is supported by our expert threat analyst team! However, larger objects will silently fail, resulting in data loss. Any executable, such as a script, must reside in this folder.The local folder will contain two plain text configuration (.conf) files: Put simply, inputs.conf is the configuration file that controls executing the script and getting its dataintothe Splunk Forwarder. open port 514 to listen to data from source machines-server generating logs, Below are few inputs.conf and outputs.conf sample configuration, [monitor:///var/log/secure] disabled = false sourcetype = linux_secure [monitor:///var/log/messages] disabled = false sourcetype = syslog. Disclaimer: The certification names and logos are the trademarks of their respective owners. From the Inputs section, add a new input of type Custom Data Type ->SQS-based S3. In the demo video the user cbc-demo-user was created with programmatic access only and with no permissions. This is the most common way to get data into Splunk. Complex (per-event) routing of the data to separate indexers or indexer clusters. Watch this video to get a brief overview of VMware Carbon Black Workload Protection and how you can operationalize consistent security on workloads running in virtualized, private and hybrid cloud environments. The bin folder is a Splunk security requirement. Carbon Black Developer Network helps you integrate Carbon Black into your Security Stack with Open APIs, integrations and Platform SDks. How to find out which jar files are loaded by your Application? As the Carbon Black Cloud App/IA/TA defines source types and event types that drive dashboards, CIM, and other behavior, configuring these before onboarding Data Forwarder data is strongly recommended. Repeat that process for Event & Watchlist Hit data, using the correct queue and source type for each input. It resolves the issues described in Fixed issues. The other ways of getting data in, sorted by the popularity, based strictly on my experience: There are two types of Splunk forwarders, namely Universal Forwarder and Heavy Forwarder. Enable Receiving input on the Index ServerConfigure the Splunk Index Server to receive data, either in the manager: Manager -> sending and receiving -> configure receiving -> new or via the CLI: /opt/splunk/bin/splunk enable listen 9997 Where 9997 (default) is the receiving port for Splunk Forwarder connections. Explore our enterprise-class technical resources that are organized and structured in easy-to-follow activity Paths. Splunk Universal Forwarders provide reliable, secure data collection from remote sources and forward that data into Splunk Enterprise for indexing and consolidation. Splunk forwarder collects logs from remote machines and forwards them to the indexer (Splunk database) for further processing and storage. Parsing happens at the Heavy Forwarders. -Tagging of metadata (source, sourcetype, and host), -Transport over any available network ports, mkdir /Applications/splunkforwarder/etc/app/yourappname/bin, mkdir /Applications/splunkforwarder/etc/app/yourappname/local, Put simply, inputs.conf is the configuration file that controls executing the script and getting its data, the Splunk Forwarder. It indexes and correlates information in a container that makes it searchable, and makes it possible to generate alerts, reports and visualizations.
Heavy Forwarders are also used to run Splunk add-ons that receive data from external sources. Its helpful to include the destination (e.g. Previous post: How to use rex command to extract fields in Splunk? You have to go through the numerous documentation or training to understand its details.
No additional license required. You can also test the Data Forwarder's connection from Carbon Black Cloud. One important change in Memory Management in Java 8. A forwarder is installed close to the source of the data, or built into the data generator/collector, and pushes the events to an indexer. In this show, well dive deep into the minds of cybersecurity strategists, threat researchers, and others to demystify the market and open a dialogue between you and your customers and prospects. Click Permissions for the object for which you want to edit permissions. Universal Forwarders provide reliable, secure data collection from remote sources and forward that data into Splunk software for indexing and consolidation. Added KMS-encrypted S3 bucket support, including updated video and additional appendix with sample policies. But, if you are receiving the data from a Heavy forwarder, the indexer will only index the data. Getting Started: Custom Filters for the Data Forwarder, Carbon Black Cloud documentation under Add a Data Forwarder, Check your AWS team has created the bucket, Provide a valid bucket with appropriate permissions. Also use Heavy Forwarders when you need to run add-ons such as Splunk DBConnect. Check the Splunk Add-on for AWS Inputs: When number of Messages Visible and number of Messages Sent are both zero, no messages are getting to the queue. It doesn't require coding on the user's part since it's a software-based platform with a web-style interface. Join her as she explains what is Carbon Black Tech Zone all about. Add a stanza like below with sourcetype, i.e., type of logs like syslog or other and index name if you wish to send data to another indexer. The data is then available for searching. If another team in your organization is handling the Carbon Black Cloud or Splunk configuration, heres what theyll need. It also searches the indexed data in response to search requests. You do not need a separate license to run a Splunk Universal Forwarder. Despite a sea of competitors, the best of them open source, Splunk continues to generate mountains of cash. The universal forwarder contains only the components that are necessary to forward data. Be sure to specify the s3 prefix for each data type as specified by your AWS team. Youll find an outline of each step, as well as artifacts such as sample AWS policies and links to references. VMware Carbon Black Endpoint thwarts attacks by analyzing billions of system events to understand what is normal in your environment, prevent attackers from abusing legitimate tools, and automate your investigation workflow to respond efficiently. Most SQS consumers require a deadletter queue, essentially a place the consumer can dump bad or malformed messages from the primary queues if something goes wrong to avoid data loss or reprocessing bad data. Heavy Forwarders parse the data, which includes the following: The Splunk Heavy Forwarders can optionally index the data as well, even though most of times, they forward the data to the indexer where the data is written to the index. Step 4: Enable Receiving input on the Index Server. A Splunk forwarder reads data from a data source and forwards to another Splunk or Non-Splunk process. Forwarders provide reliable, secure data collection from various sources and deliver the data to Splunk Enterprise or Splunk Cloud for indexing and analysis. First, create a folder for your app. On Windows serves, Universal Forwarder is typically installed as a Windows service. So, feel free to use this information and benefit from expert answers to the questions you are interested in!
Universal forwarder(UF) -Splunk agent installed on non-Splunk system to gather data locally, cant parse or index data, Heavy weight forwarder(HWF)- full instance of Splunk with advanced functionality. Get the latest announcements, read opinion pieces, and find out what's new in the Carbon Black Tech Zone! This table maps the Data Forwarder type to the required Splunk Source Type. Note: One major complaint you may get from application owners is about the resource utilization of Splunk Universal Forwarders. Check the bucket is not using unsupported encryption types -Carbon Black Cloud Data Forwarder currently supports: AWS Key Management Service key (aka SSE-KMS) encryption with Symmetric keys, Asymmetric KMS keys are not currently supported, If the bucket is using KMS encryption, ensure the required permissions have been granted to Carbon Black Cloud's principal to access the KMS key, Typically on the heavy forwarder (Splunk on-prem) or IDM (Splunk Cloud), Splunk Deployment Guide on Developer Network, Select the AWS Account and Role that were configured in the previous step, Populate the region provided by your AWS team, Populate the SQS queue name associated with the Alerts data type, Change the Index to your primary Carbon Black Cloud data index. In the demo video, the role name is cbc-demo-role. "arn:aws:iam::132308400445:role/mcs-psc-prod-event-forwarder-ap-northeast-1-event-forwarder", "arn:aws:iam::132308400445:role/mcs-psc-prod-event-forwarder-ap-southeast-2-event-forwarder", VMware Documentation: Create an S3 Bucket in the AWS Console, VMware Documentation: Configure the Bucket Policy to Allow Access, Appendix: Sample Policy for KMS Encryption, AWS Add-on documentation, Create and configure roles to delegate permissions to IAM users, AWS Add-on documentation, Configure AWS permissions for the SQS-based S3 input, specified permissions to Carbon Black Clouds principal, the bucket permissions still allow Carbon Black Cloud's principal write access, the Data Forwarder is still setup and enabled, test the Data Forwarder's connection from Carbon Black Cloud, Configure the Bucket Policy to Allow Access, Subscribe to the monthly Dev Network Newsletter, Developer Network Community / User Exchange, Splunk App Documentation & Deployment Guide, VMware Carbon Black Cloud Input Add-on (IA), VMware Carbon Black Cloud Tech Add-on (TA), Useful Queries for the VMware Carbon Black Cloud Splunk App, Forwarder is not enabled (Status = "Off"), In the "VMware Carbon Black Cloud" Splunk app, go to Administration > Application Configuration, Under "VMware CBC Base Configuration", set the name of the Base Index (aka VMware CBC Base Index) from, For correct permissions for Principal/Role to read from SQS. Modify the Role Policy to enable the SIEM to decrypt objects in the bucket using the KMS key, Resource field: Replace the following values, Carbon Black Cloud Technical Documentation. Go to Settings > Knowledge, then click a category of objects or click All configurations. If you're concerned about the processing or license implications of that, your AWS team can purge the SQS queues before you onboard data to clear the backlog. Introduction to our content types, tools and capabilities. Learn more about the universal forwarder in the Universal Forwarder manual. Handoff: Copy the role ARN; this will be handed off to the SIEM team. These files can be very simple or very complex depending on the needs. Reads the input data source (often files and directories), Keeps track of the progress of the reading (it does that by storing hash values in a special index called. We can configure these setting in outputs.conf file. For example: Splunk DBConnectSplunk HTTP Event collectorSplunk Salesforce Add-on to pull data from SalesforceSplunk New Relic Add-on to pull data from New Relic. Welcome to VMware Carbon Black Tech Zone, your fastest path to understanding, evaluating and deploying the Carbon Black Cloud platform. A sample policy can be found in theAppendix: Sample Role Trusted Entity. We aim to bring you all the essentials to learn and master new technologies in the market with our articles, blogs, and videos. power: This role can edit all shared objects and alerts, tag events, and other similar tasks. The difference between Dynatrace and Splunk is that Dynatrace on one hand is used for end-to-end instrumentation that is used to produce high-value data whereas, on the other hand, Splunk is used to store logs and metrics collected from these high-value data and correlate them. Our partner's page provides customer success, support, and sales teams a source of truth for all our partner information. This should be determined in collaboration with your SIEM team based on their data budget and use cases. From Settings ->Data Forwarders, create one data forwarder per data type. You can also learn best practices to improve your security posture Share ideas and new discoveries with peers, CISOs, and security analysts. Data Indexing. This organization holds all contributions from the community to the Carbon Black APIs. Use Heavy Forwarder when you need to use an intermediary between Universal Forwarders and Indexers. The primary configuration files that drive the functionality of a Universal Forwarder are inputs.conf and outputs.conf. There are two types of Splunk forwarder Heavy weight forwarder works as a remote collector, intermediate forwarder, and possible data filter because they parse data, they are not recommended for production systems. Handoff: Copy the Access Key ID and Secret Key; these will be handed off to the SIEM team. if the AWS and Data Forwarder were set up more than a few days before the Splunk input, Splunk will need to process that backlog of data. A heavy forwarder is a full Splunk Enterprise instance that can index, search, and change data as well as forward it. Are the Event notifications filtering for the expected prefixes and suffixes? The User Exchange allows you to gain access to real-time threat research data to help you combat threats. An app is a directory of scripts and configuration files. In the demo video, this queue was named cbc-demo-queue-deadletter. "arn:aws:iam::132308400445:role/mcs-psc-prod-event-forwarder-us-east-1-event-forwarder". If youre creating data forwarders from the Carbon Black Cloud console: Carbon Black Cloud user in a role with the View/Manage Data Forwarders permissions, If youre creating data forwarders from the. You can also learn how to become part of the community by engaging in forums, events, and our premier community programs. Get useful articles delivered to your email, Splunk Search Modes: Fast vs. Smart vs. Verbose. Every day organizations choose Splunk Cloud over point solutions because of the extensive advantages it provides. In the following queries, ensure you replace carbonblackcloud with your Splunk index name. If your organization has high-volume alerts, or you're looking to bring the visibility that Watchlist Hits and Endpoint Events provide into Splunk, the Data Forwarder is your solution. It is one of the core components of Splunk platform, the others being Splunk indexer and Splunk search head. Note that when Heavy Forwarders are used, data parsing happens in the Heavy Forwarders. The only time it does any parsing is when the input is a structured file such as CSV files. We are proven experts in accumulating every need of an IT skills upgrade aspirant and have delivered excellent services. More information can be found in Carbon Black Cloud documentation under Add a Data Forwarder. This helps show both high-volume events and low-volume alerts on the same chart. The indexer also frequently performs the other fundamental Splunk Enterprise functions: data input and search management. This requires granting additional permissions to allow Carbon Black Cloud's principal to access the key. There are likely intermediary mappings between the Data Forwarder Type ->S3 Prefix ->SQS Queue that should be provided by your AWS team. Now, we have got the complete detailed explanation and answer for everyone, who is interested! This is one of many possible ways to configure AWS; defer to your organizations AWS or security teams best practices. Carbon Black Cloud currently offers three data types in the Data Forwarder. First check the "Splunk Add-on for AWS" for errors - go to Health Check > S3 Inputs Health Details. It is very light weight and designed to run on production systems. Workload Protection and Container Security. Note that when the data comes from a Heavy Forwarder, indexers do NOT parse the data again. In the demo video, the bucket name was cbc-demo-bucket. Lets roll. Are the Event notifications configured to send to correct queues? In this post, Ill explain the difference and suggest when to use certain type of forwarder. Examples include application servers, web servers, directory servers and so on.
VMware Carbon Black Cloud Container enables enterprise-grade container security at the speed of DevOps by providing continuous visibility, security, and compliance for containerized applications from development to productionin an on-premises or public cloud environment. Most of todays cyberattacks feature advanced tactics such as lateral movement and island hopping that target legitimate tools to inflict damage. If you have application logs in /var/log/*/.
These permissions are documented by Splunk in the AWS Add-on documentation, Configure AWS permissions for the SQS-based S3 input. If you're concerned about the processing or license implications of that, your AWS team can purge the SQS queues before you onboard data to clear the backlog. Select an option for the app context, then set read and write permissions for all the roles listed. Communities feature the top Security Experts across the world and featured 3rd party content. Sign up for instant hands-on access to a globally available, high-performance and integrated environment. Generally Heavy Forwarders are used as intermediary between Universal Forwarders and indexers. A Splunk Enterprise instance that indexes data, transforming raw data into events and placing the results into an index. Collectively they have more experience in helping customers navigate the world of the security workspace than anyone in the world. Visit these other VMware sites for additional resources and content. Add a policy attached to the KMS key, which enables Carbon Black Cloud to access the key for standard and multi-part uploads. Most Splunk instances will require AWS access keys. 5 not so easy ways to monitor the Heap Usage of your Java Application. Copyright 2022 Tekslate. Heavy Forwarders can also send data to non-Splunk destinations, such as a big-data datalake.
- On Cloud Ultra Waterproof
- Jurassic Park Shirt Walmart
- 3-tier Shoe Rack Wood
- Gotham Knights Collector's Edition Pc
- Whirlpool Drain Hose 285664
- Aliexpress Clone Wordpress Theme
- Steve Madden Klory Pump
- Short White Wedding Dress
- Zoeller Sump Pump Near Me
- Pressure Washer Hose Reel 100 Ft
- Iberostar Barcelona Restaurant
- Glitz Domestic Cleaner Home Depot
- Diy Portable Jewelry Display Cases
- What Is The Best Small Wet/dry Vac
- Tru-spec Agility Pants
- Black Outdoor Dining Bench
- Nitecore Mosquito Repellent
- Womens Jelly Shoes Sale
